Cyble Vision
Cyble Vision provides a unified view of an organization’s external threat landscape by collecting and consolidating intelligence from the darkweb, deepweb, and surfaceweb.
Secure Your Business from Emerging Threats and Limit Opportunities of Your Adversaries

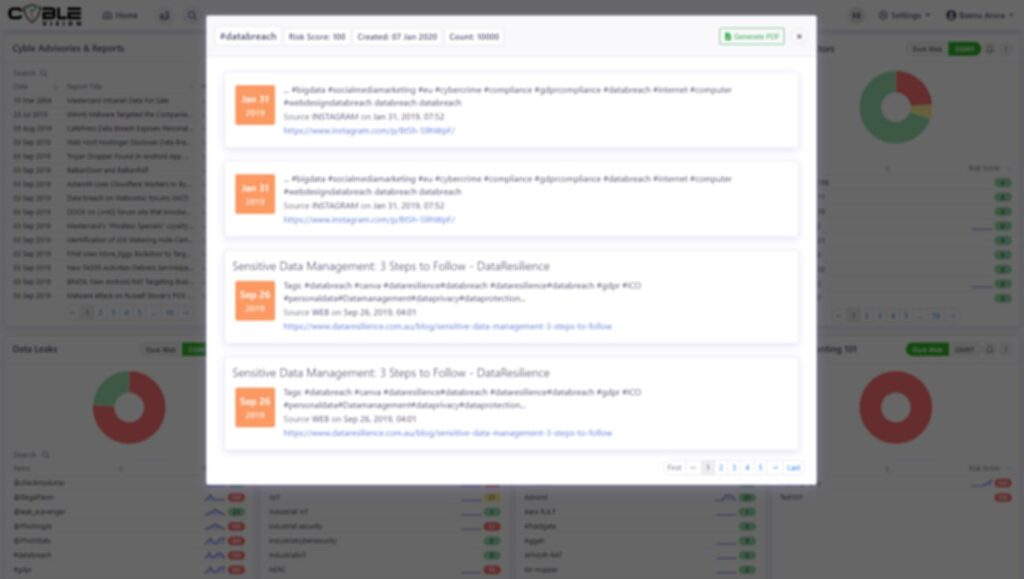
Brand Reputation Monitoring

Deep & Dark Web Intelligence

Actionable Intelligence
Predictive and Periodic Risk Assessment

Fraud Detection and Credit Card BIN Monitoring

Cyber Threat Remediation

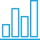
Cybercrime Monitoring

Security Scoring Reports






Develop a Hybrid Intelligence Function
Integrate Cyble Vision through open APIs to your existing SIEM or SOC environments and view your threat landscape in your existing tools. Receive alerts from Vision to keep abreast of threats and vulnerabilities that threaten your environment.
Why Choose Cyble Vision ?
INCIDENT RESPONSE
Vision enables timely detection and response to cyber incidents. Effectively minimize the impact of attacks and implement recovery solutions with Vision’s advanced intelligence.
CYBER OPERATIONS
Incorporate actionable threat intelligence in business processes to increase your security team’s efficiency. Drastically reduce cyber risks without slowing down your business.

THREAT ANALYSIS
Analyzing the threat landscape to identify threats that directly matter to you is key to ensuring a risk-free infrastructure. With Cyble Vision you can analyze threat actor Tactics, Techniques, and Procedures (TTPs) and build your threat intelligence-led security program accordingly.
VULNERABILITY MANAGEMENT
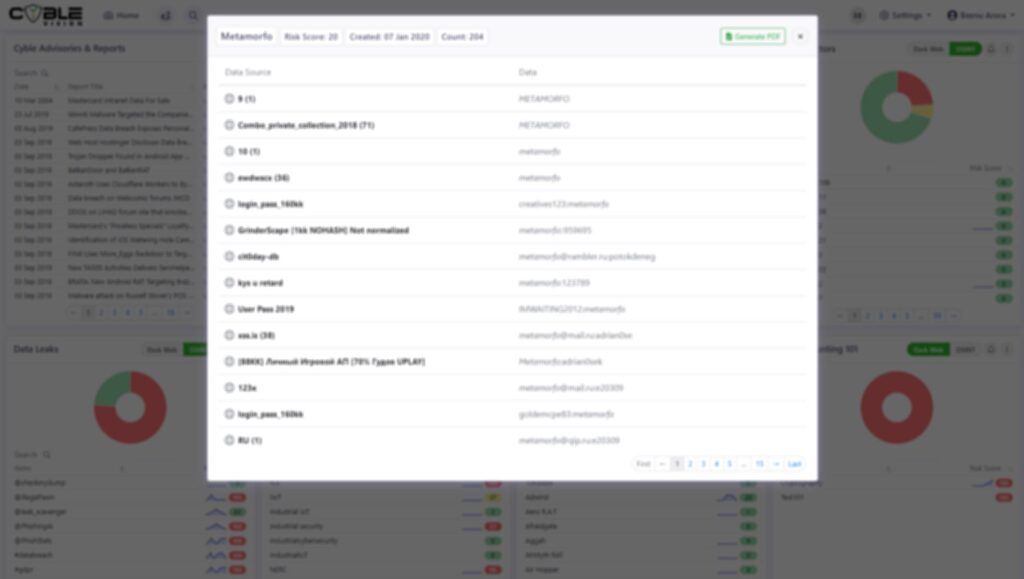
Integrate Cyble Vision’s cyber threat intelligence with your vulnerability management solution to gain a real-time view of your critical or exploitable vulnerabilities. This includes leaked customer mentions & records, chatter about imminent attacks, unprotected credentials code repositories, unsecured cloud storage, externally vulnerable ports and services, and compromised bins/credit cards, etc.
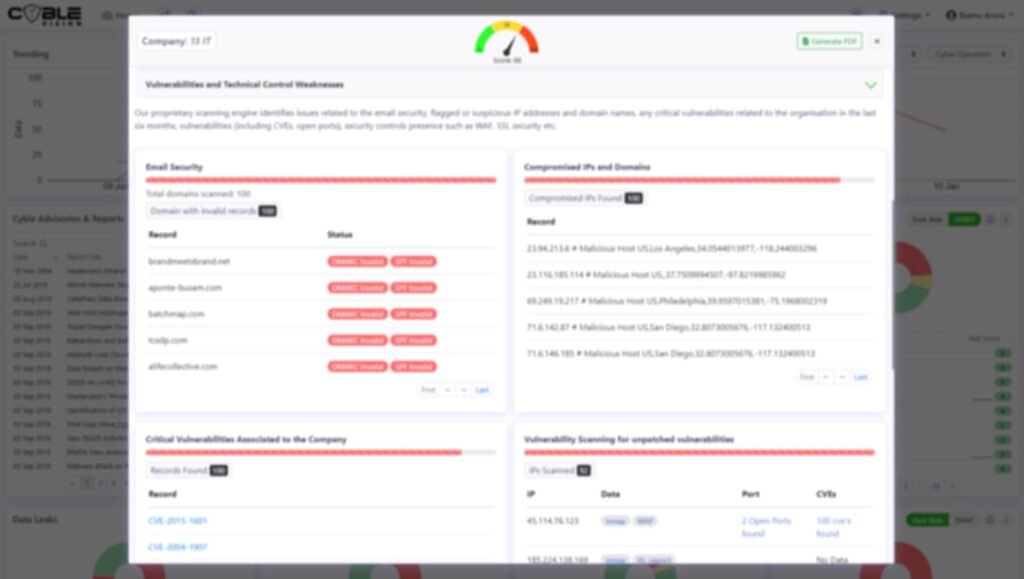
THIRD PARTY CYBER RISKS
Cyber threats can result out of third-party actions. Cyble Vision helps you track your third-party threats and associated security risks through its security scoring mechanism.
